T-Pot Honeypot: The All-in-One Cybersecurity Trap
In an age where cyber threats evolve faster than ever, defenders need proactive tools to detect and analyze malicious behavior. One powerful tool in the defender’s arsenal is the honeypot—a decoy system designed to attract and analyze attackers. Among the most advanced honeypot solutions available today is T-Pot, an all-in-one honeypot platform developed and maintained by Deutsche Telekom Security GmbH.
What Is T-Pot?
T-Pot is a multi-honeypot platform that integrates several well-known honeypot technologies into a single, easily deployable system. It leverages Docker containers for isolation and ease of deployment, combining the functionality of multiple honeypots with logging, visualization, and management tools.
With T-Pot, you don’t just detect an attack—you watch it happen, analyze the behavior, and collect intelligence that can be used to harden your real systems.
Why Use T-Pot?
Traditional security measures such as firewalls and antivirus software are often reactive. T-Pot, on the other hand, offers a proactive approach. Here’s why T-Pot stands out:
- Comprehensive Coverage: T-Pot combines multiple honeypots like Cowrie (SSH/Telnet), Dionaea (malware collection), Glastopf (web vulnerabilities), and more.
- Modular & Scalable: Thanks to Docker, each honeypot runs in a separate container, making it easy to add, remove, or update components.
- Visualization Tools: It integrates tools like Kibana, Logstash, and Elasticsearch (ELK stack) for real-time data visualization.
- Security Intelligence: Captured payloads, attacker IPs, and behavior patterns can be used for threat intelligence and security research.
- Open Source: T-Pot is freely available under the Apache 2.0 license, with an active community contributing to its development.
Features at a Glance
Here are some of the key components often bundled with T-Pot:
| Component | Functionality |
|---|---|
| Cowrie | SSH/Telnet honeypot for capturing login attempts |
| Dionaea | Malware capture for SMB, HTTP, and FTP threats |
| Conpot | Simulated industrial control systems (ICS) |
| Honeytrap | Low-interaction honeypot for network-level traps |
| Elastic Stack | Centralized logging and dashboard visualization |
| Suricata | Intrusion detection and traffic analysis |
How T-Pot Works
- Deployment: T-Pot can be deployed on a dedicated server or virtual machine. A base installation of Ubuntu Server is required.
- Configuration: After installation, the platform initializes Docker containers for each honeypot and supporting service.
- Operation: T-Pot starts listening on commonly attacked ports. When an attacker interacts with these services, their actions are logged and visualized.
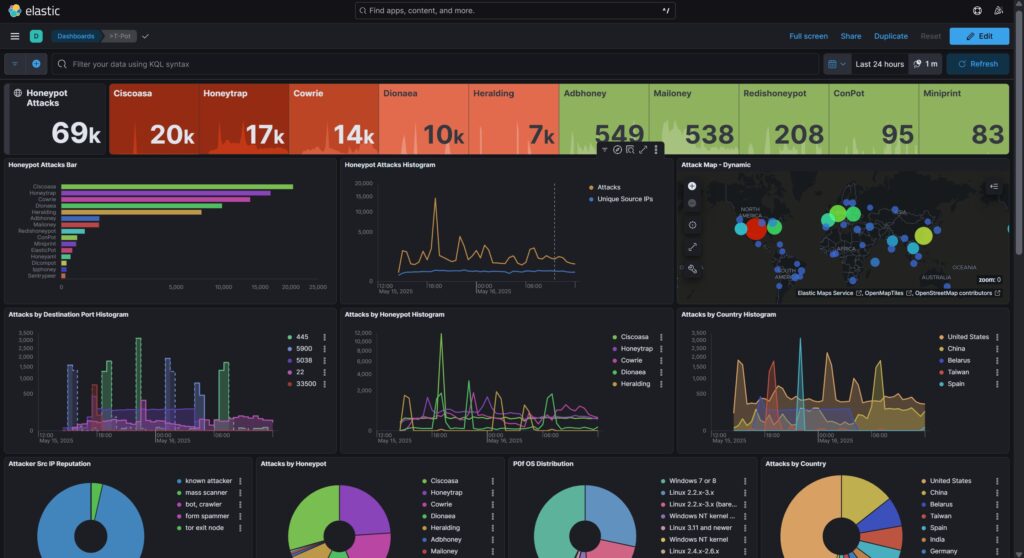
- Analysis: Using Kibana dashboards, you can analyze attack patterns, payloads, and attacker origins.
Deployment Tips
- Isolate It: Run T-Pot in a secure, segmented network—preferably outside your production environment.
- Limit Access: Only allow administrative access to trusted users via VPN or secure tunnels.
- Monitor Regularly: Check dashboards for new activity and update honeypot services frequently.
Use Cases
- Threat Intelligence: Gather real-world data about attacker behavior and emerging malware.
- Security Awareness: Use T-Pot as a teaching tool in cybersecurity training environments.
- Incident Response: Identify and understand new attack vectors to inform incident response strategies.
- Research: Conduct academic or corporate research on attack patterns and malware evolution.
Final Thoughts
T-Pot is not just a collection of honeypots—it’s a powerful ecosystem for security monitoring and threat intelligence. Whether you’re a researcher, SOC analyst, or cybersecurity enthusiast, T-Pot gives you the tools to turn the tables on cyber attackers.
If you’re serious about understanding the threats targeting your network, setting up a T-Pot honeypot is one of the best investments in visibility you can make.
